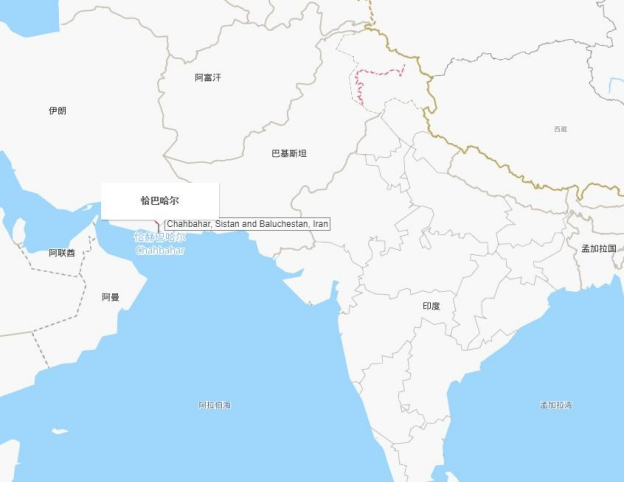
Recently, ThreatBook has captured several APT attacks targeting countries in South Asia and the Middle East mainly involving the tripartite member states who signed the “Chabahar Port Agreement”, including Iran, Afghanistan, and India. The attack shows obvious national strategic purpose. The historical espionage activities carried out by the Group can be traced back to at least 2013. The Group is good at using phishing and watering hole attacks. The attack platform involves both PC and mobile client with the open-source Trojans as the main tool. And at the same time, it also has certain development capabilities with its own steal backdoor. Chabahar Port, also known as Chabahar, is located on the coast of Sistan-Baluchistan Province at the southeastern of Iran, with the Arabian Sea main channel of the maritime hub in the south and Pakistan in the east. To the west is the coast of the Persian Gulf, the global oil and gas center, and to the north leads to the oil-rich Central Asian. The Port is just at the intersection of West Asia, South Asia, Central Asia, and the Indian Ocean with the great importance of geographical transport. The city Chabahar where the Port is located, is the military center of Iranian navy and air force. Iran has many large iron mines and giant copper mines and rich oil and gas resources. And Afghanistan which is close to Iran also has Asian largest iron mine and world-class copper mine. India and Afghanistan, which participated in the signing of the Chabahar Port Agreement, have long been constrained by Pakistan in land transportation. The establishment
of the Chabahar Port opens a new strategic channel for India, Afghanistan, and Iran. Chabahar Port is less than 100 kilometers away from the China-Pakistan Economic Corridor – Gwadar Port, known as the Indian version of the Belt and Road.
ThreatBook Intelligence Research and Response Team have specific findings as follows:
· The Group behind this attack has been active for at least 13 years, and the attack area covers Iran, Afghanistan, India and Pakistan, involving human rights activists, transportation department, military, veterans, extremists and government agencies, etc.; · The delivered backdoor has the attack capability on both PC and Android platforms. The PC platform uses PrisrolRAT and QuasarRAT backdoors, and the Android platform uses AndroRAT backdoor; · In terms of asset Whois information, AndroRAT Trojan configuration, attack targets and regions, it was found that there is a certain overlap between the Group and the TransparentTribe, and it is suspected that is also has a Pakistani background; · ThreatBook extracts 25 related IOCs though the traceability analysis of related samples, IPS, and domain names, which can be used for threat intelligence detection. TDP, TIP, API, OneDNS of ThreatBook have all supported the detection of this attack activity and group.
Details
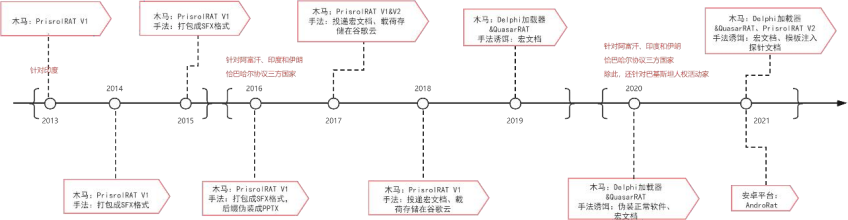
Recently, ThreatBook have captured several attacks, including the use of phishing attacks and watering hole attacks to deliver malicious bait file and malicious installation packet masqueraded as normal software targeting Windows platform, as well as malicious APP masqueraded as normal Android app stores to induce victims to download. After correlation analysis, it is found that the historical espionage activities of the Group behind can be traced back to at least 2013. The early attacks targeted the Indian region, and after the three parties: India, Afghanistan and Iran officially launched trade exchanges as the signing of the Chabahar Port Agreement in 2017, Iran, Afghanistan and the Iran-Pakistan border – Baluchistan area were also included in the attack range. These attacks mainly involve human rights activists, the transportation department, military department, veterans, extremists, and government departments. Through the traceability analysis, it is found that the configuration information of the mobile backdoor captured recently has the same configuration as the backdoor recently used by TransparentTribe, which means there may be some connection between the two Group. This attack has a strong purpose with a national strategic purpose, and it is suspected to be carried out by an APT group supported by the state. Activity feature timeline:
Sample Analysis
The malicious samples found in this attack involved Windows and Android platforms. The Windows platform uses various types of malicious samples for phishing and watering hole attacks. The open-source Trojan QuasarRAT and the Delphi Trojan named PrisrolRAT are mainly used as Trojan backdoor. The samples from Android platform use the open-source AndroRat Trojan, and
its method is to induce the victim target to download and run the Android software download store which is masqueraded to be a normal one. Windows platform
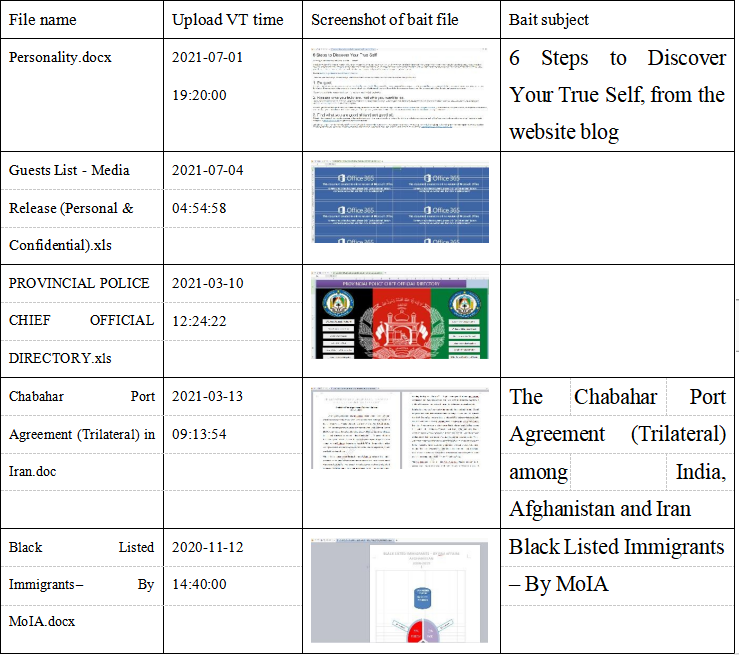
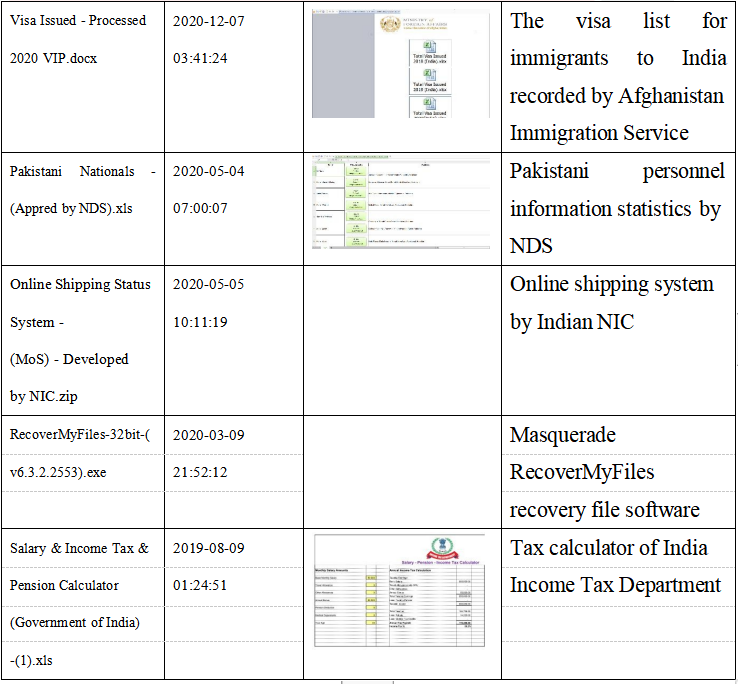
1.There are four types of malicious samples from Windows platform: bait compress packet with Trojan, an executable self-extracting bait program and two types of malicious files. One of the malicious files releases backdoor by enabling macro. And the other has the same principle as template injection, but instead of downloading malicious files, it is used as a probe. 2.Recent samples:
3.Probe file samples analysis
1)Basic information
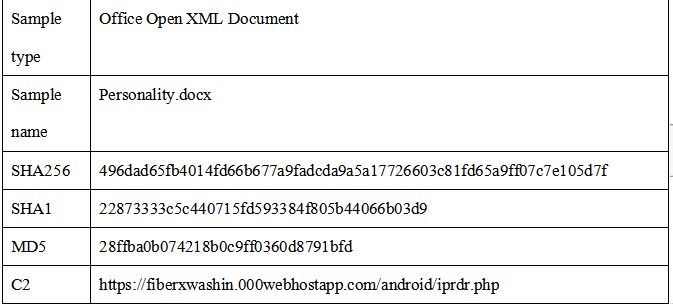
2)Sample analysis
a)After opening the malicious file, the remote template link is to be triggered, and is to access the embedded URL link https://fiberxwashin.000webhostapp.com/Android/iprdr.php, but no download follow-up is returned. It is speculated that the role of the sample is to use the probe to acquire anti-linking information.
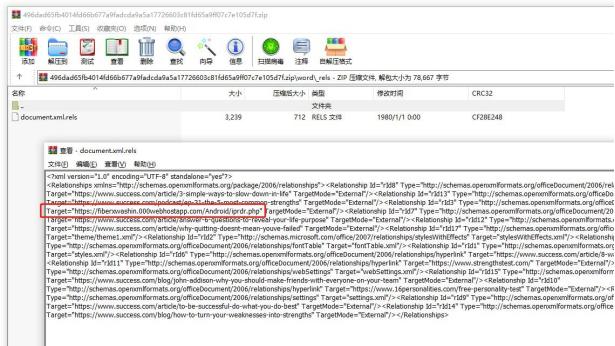
4.Macro file type 1 sample analysis
1)Basic information
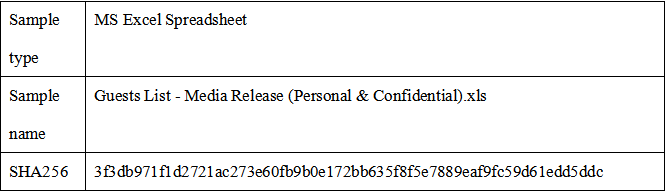
2)Sample analysis
a)The sample carries the macro code to decode the Base64 encoded payload and release the file. Then execute the file and release the directory “%appdata%\Microsoft\update\modules\csrss.exe”.
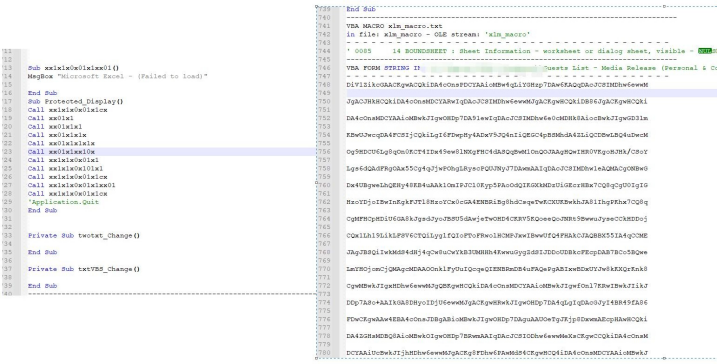
b)“csrss.exe” is written by Delphi with the function to steal the target data files. The malicious code is triggered by multiple clock incidents. In the window Create incident, persistence is achieved by writing the Run in the registry (startup item name: “Microsoft Modules Patcher”).
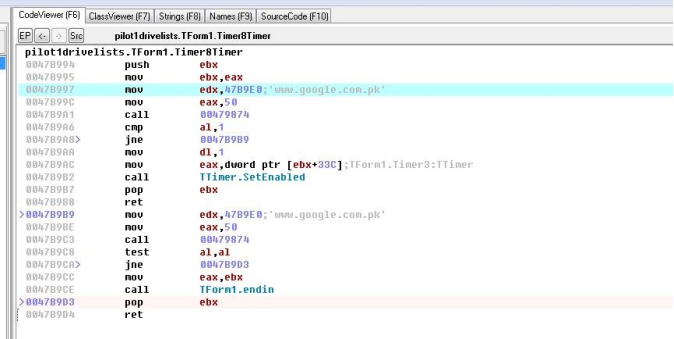
c)Check www.google.com.pk for connection.
d)Initialize the directory of C2 server (the C2 file is uploaded without checking file suffix), acquire computer information including process info, software info, hardware info, system version, which are stored in the Text of the control, in HTTP call GetText to get the data out and send it to server.
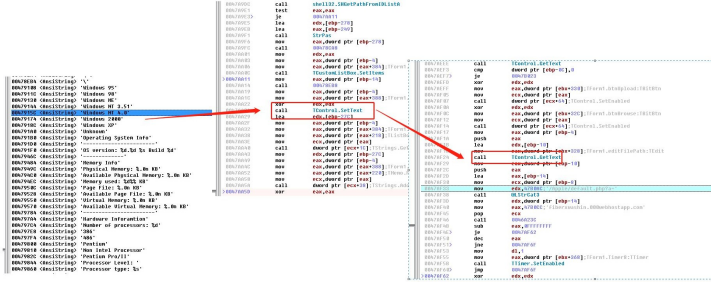
e)Loop to acquire the"/fil" of the C2 server, which stores the file suffix, such as “*.doc”.
Then scan and upload the files with the same suffix by local program.
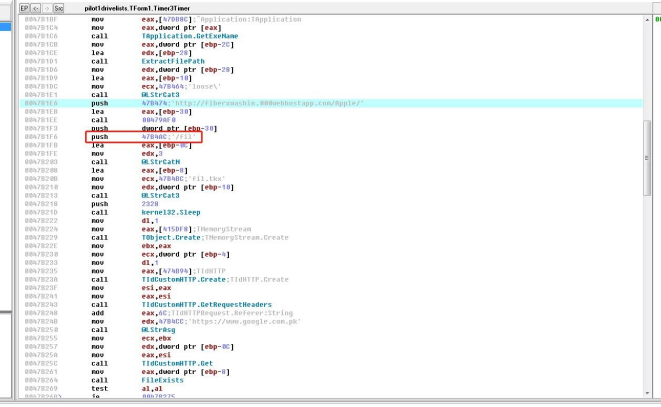
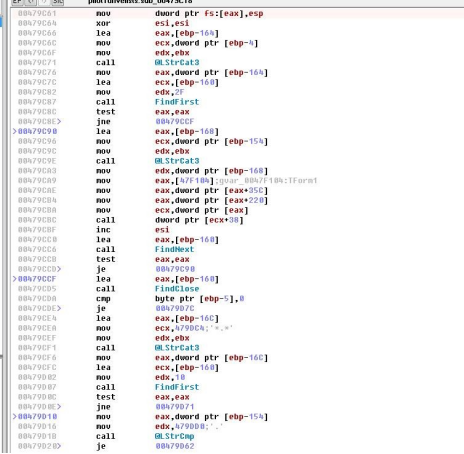
f)Traverse the files to acquire files with a specific suffix.
5.Macro file type 2 sample analysis
1)Basic information
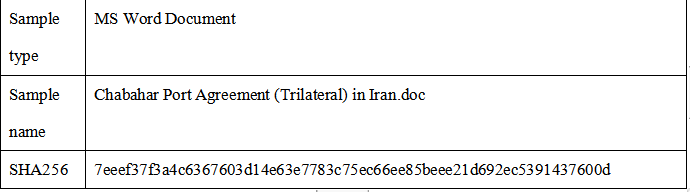


2)Sample analysis
a)This sample carries the same macro code as the above. Decode the Base64 encoded payload and release the file. Then execute the file and release the directory “%appdata%\msword.exe”
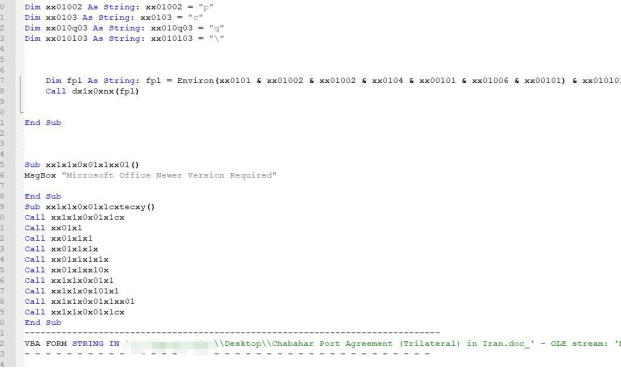
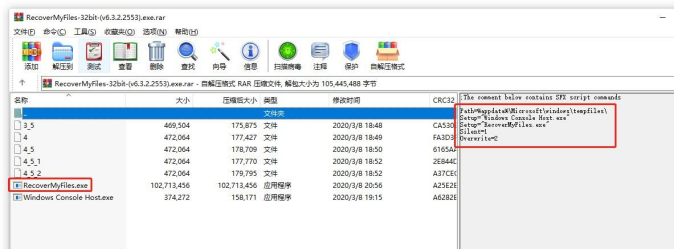
b)“msword.exe” is a compressed file of SFX type, which is to release the Delphi loader and the QuasarRAT backdoor after being executed.
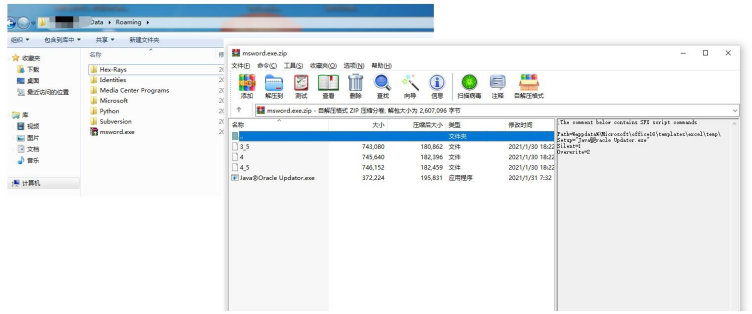
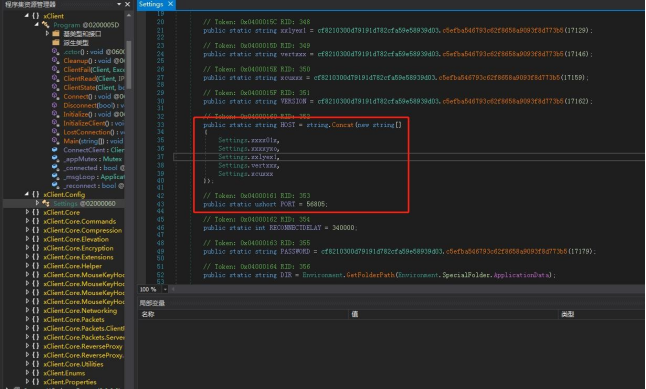
c)“JavarOracle Updator.exe” is a Delphi loader which is executed by the command-line of SFX. After running, it will look for the existence of “3_5”, “4”, “4_5” files in the same directory. If any file exists, it will be renamed “juschaid.exe” and written to the Run startup item of the registry.
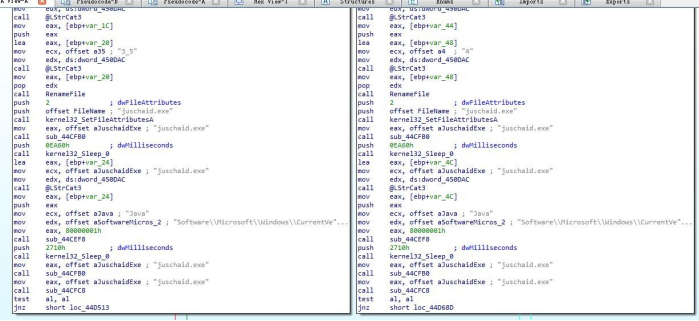
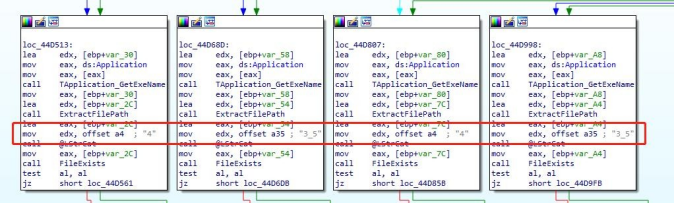
d)“3_5”, “4”, “4_5” are QuasarRAT Trojans, C2: “faqeera-56805.portmap.io: 56805”
e)The function supported by QuasarRAT is as follows:
· TCP network flow (support IPv4 and IPv6) · Fast network serialization (protocol buffer)
· Compressed (QuickLZ) and encrypted (TLS) communication
· Multithreading · UPnP support
· No-Ip.com support
· Visit website (hidden and visible) · Display message box
· Task manager
· File manager
· Startup manager
· Remote desktop
· Remote shell
· Download and execute
· Upload and execute
· System information
· Computer commands (restart, shutdown, standby)
· Keylogger (Unicode support)
· Reverse proxy (SOCKS5)
· Password recovery (universal browser and FTP client)
· Registry editor
6.EXE sample analysis
1)Basic information
2)Sample analysis
This sample is same as the SFX released by“macro file type 2 sample analysis”. The difference is that this sample is delivered as data recovery software, while SFX will install normal data recovery software as executing the backdoor
·Android platform
1.Through the multi-dimensional association of asset domain names, it is found that there is a malicious APK sample in one of the links. After the retrieval of ThreatBook bigdata platform, it is found that the APK sample induces user to download by masqueraded APKPure app store.
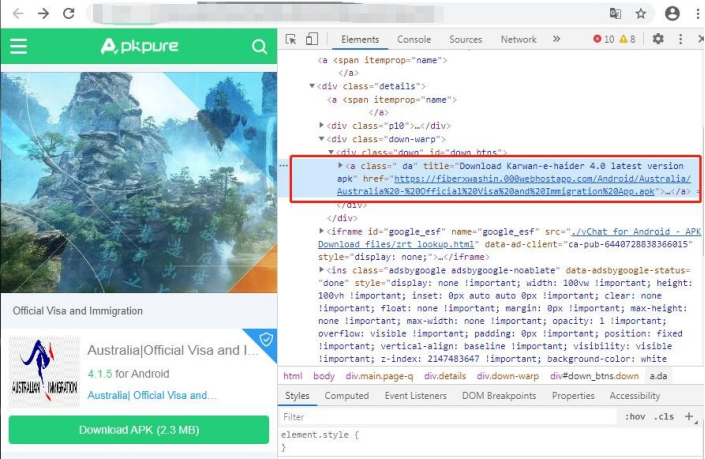
2.According to the feature analysis of the masqueraded APKPure store, it can be traced back to multiple masqueraded malicious APK samples
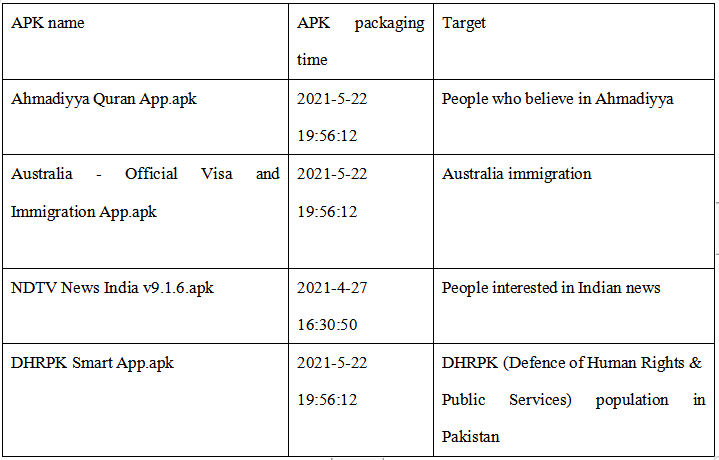 .
.
3.Sample analysis
1)Basic information
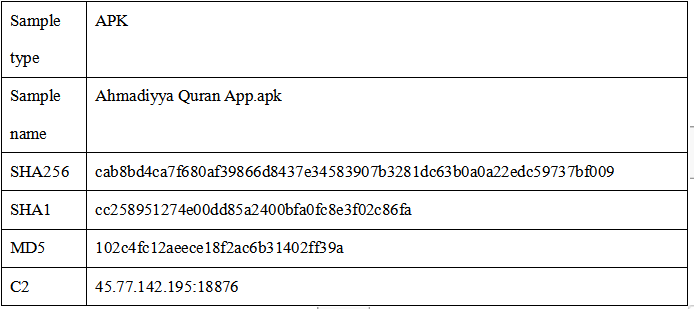
2)Comparing the code features of the sample, it is found that the sample is isogeny to the open-source Trojan AndroRAT as a variant.
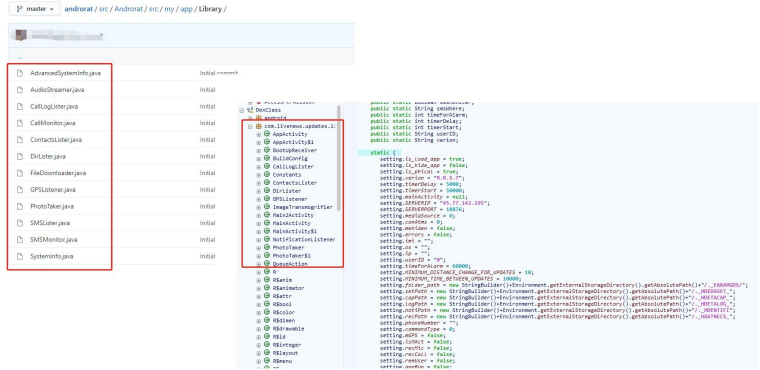
3)The function of AndroRAT includes at least: contact information acquisition, call information acquisition, SMS information acquisition, GPS/network positioning, real-time monitoring to receive SMS, real-time mobile phone status acquisition, taking picture, ringing, recording videos, sending text messages, making calls, opening the browser, and phone vibrating.
Association of Historical Attacks
After the relevant samples analysis, backtracking of attacks through ThreatBook source tracing platform and bigdata platform, it is found that the attacks of the Group can be traced back to at least 2013, and since 2017, it has used the relevant topic on the three parties who signed “Chabahar Port Agreement” to attack, such as “Baloch missing persons contact list”, “Afghanistan-India-Iran Strategic Policy Members”, “List of Key Stakeholders in Afghanistan, India and Iran”. It is found that the Group started to use the backdoor developed by Delphi to carry out attack activities as early as 2013 by the code isogeny. According to the “prisrol.dev” string appeared in the backdoor in the early stage, ThreatBook named the backdoor PrisrolRAT, and classified it into two version V1 and V2 according to the different functions. Historical sample traceback:
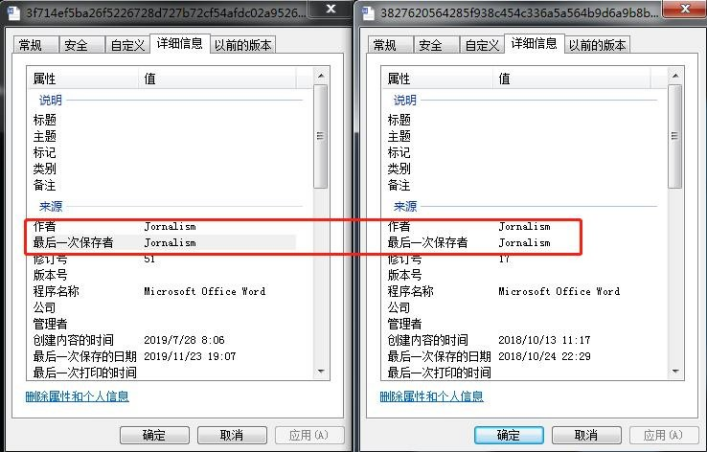
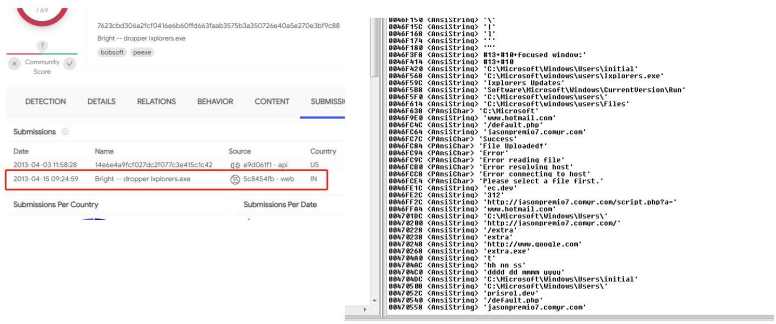
1.During the analysis of the recently captured samples, it is found that the author name of a relevant sample is quite special. It is an attack sample used in 2018 found by searching through the bigdata platform.
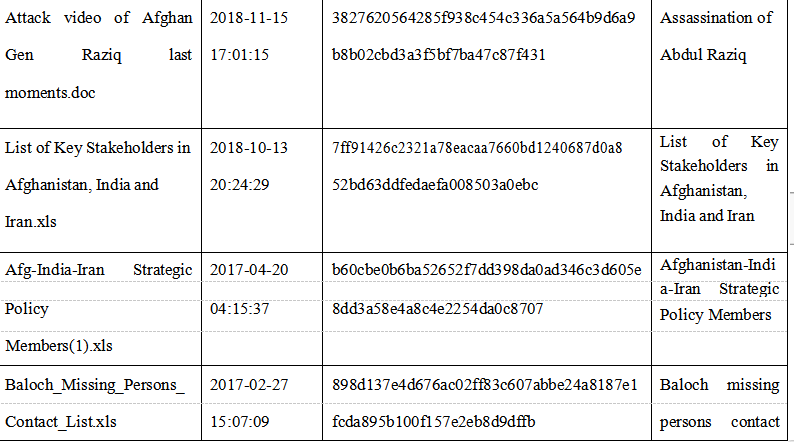
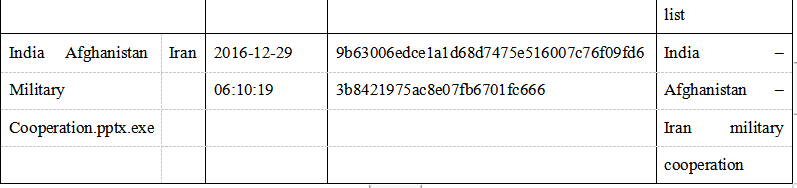
2.With further correlation analysis of the associated historical malicious sample macro code metadata and assets, it is found that a batch of bait used in the Group attack activities from 2017 to 2018. 3.Parts of the bait are as follows:
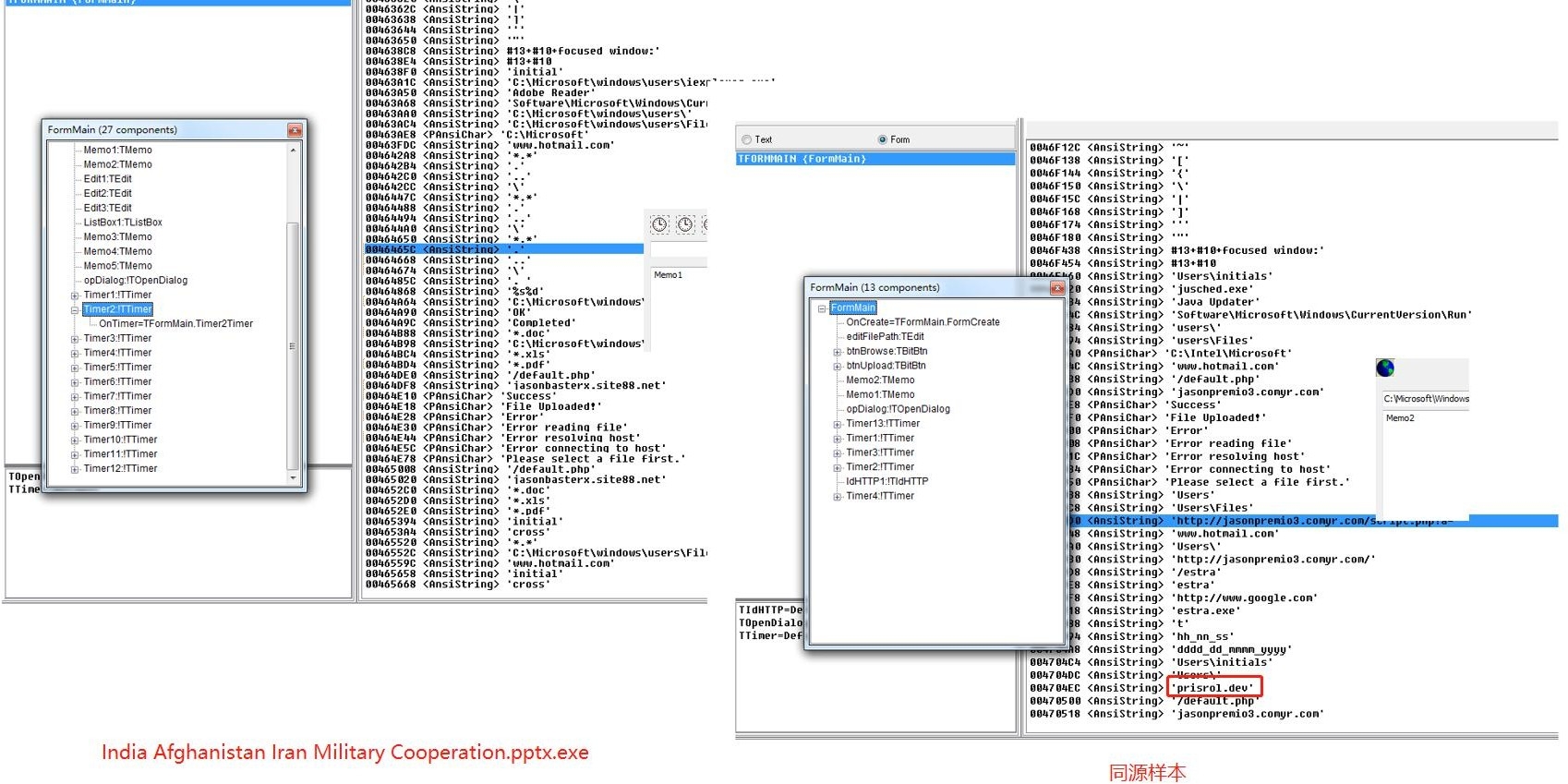
4.After the analysis of the sample “India Afghanistan Iran Military Cooperation.pptx.exe”, it is found that the released backdoor was the Delphi stealing Trojan, whose isogeny sample has “prisrol.dev” string, so it is named PrisrolRAT V1.
5.In addition, during the comparison of the Delphi backdoor in the recent attack, it is found that the backdoor has a certain similarity with the code of PrisrolRAT V1 and a high similarity with the assets. So, the Delphi backdoor used in recent attacks is named PrisrolRAT V2. And comparing the two versions, though there are certain differences between V1 and V2, both can achieve the function of stealing files. 6.Version differences. In the V1 version, the stolen file types are fixed as xls, jpg, ppt, iaf, and it also has keylogging function which is removed in the V2 version. And in the V2 version, the file type is determined by the fil file on the server, and the backhaul of system information has been added.
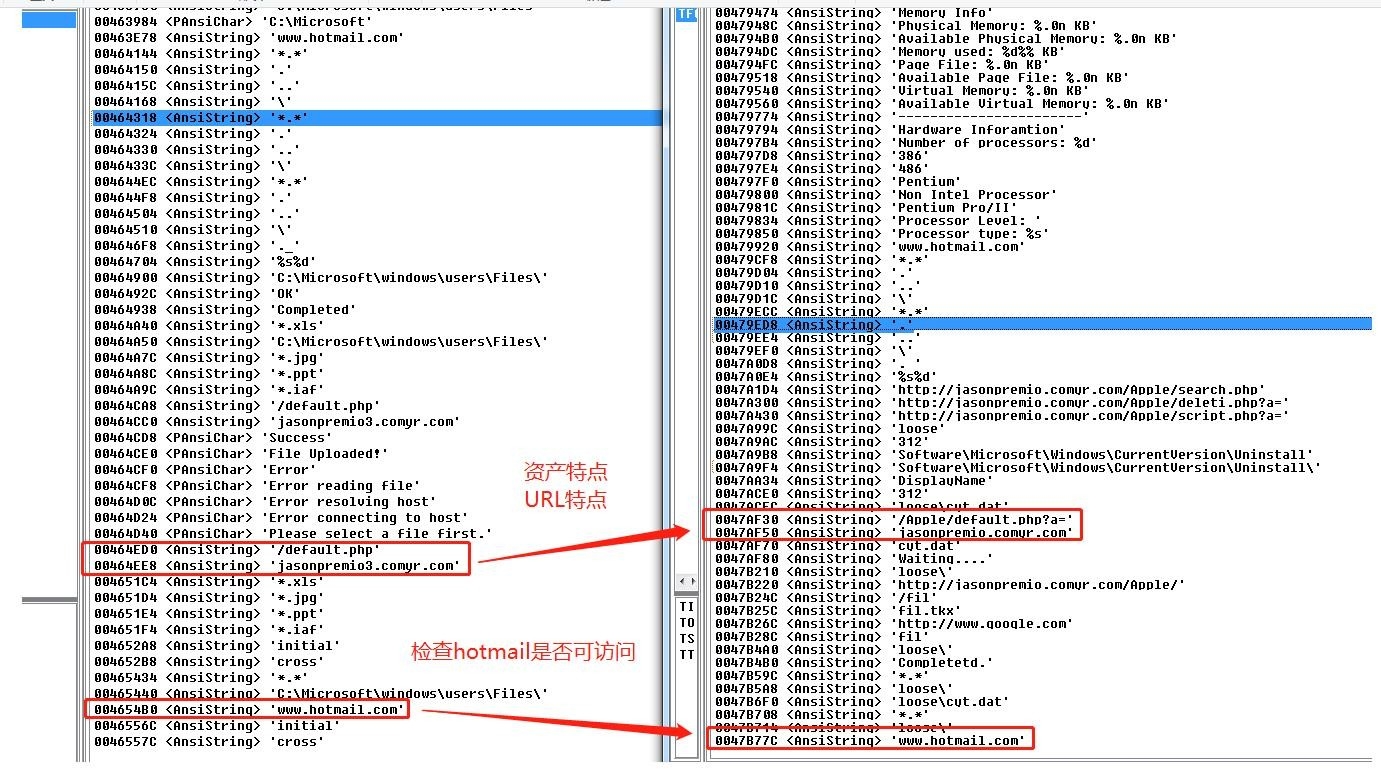
7.In addition, a large number of PrisrolRAT samples are found to have URL request features such as “/script.php?a=”. And through the ThreatBook isogeny URL hunting system, some suspected request URLs of the Group are found.
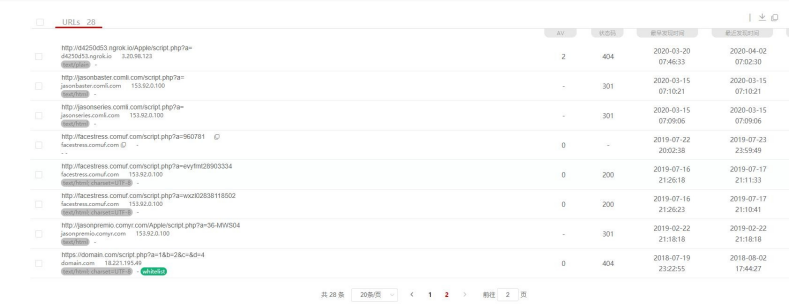
8.After checking the suspected isogeny URLs, sieving the early assets of the Group, a communication sample in one of the domain names has been found. After analysis, its version is found to be PrisrolRAT V1 with upload time in April 2013.
Group Attribution
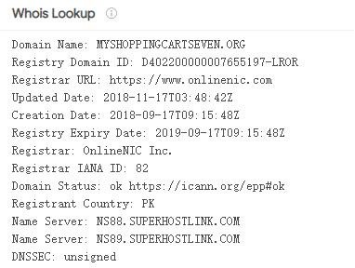
1.The asset domain name“myshoppingcartseven.org”used in historical activities , and the registered country in the historical Whois information is Pakistan.
2.An APK sample with a completely consistent configuration is found on the domain name“shareboxs.net” commonly used by TransparentTribe APT. The APK upload time is in May 2021, which indicates there is a certain association between the two Group.
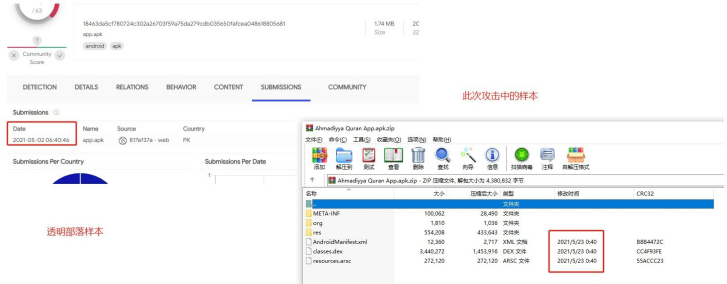
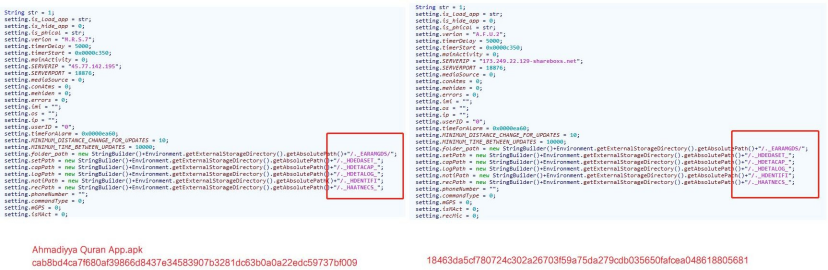
3.During the analysis of the file type bait template used in the 2017-2018 attacks, a batch of samples using the same template are found, namely the TransparentTribe using CrimsonRAT and the Donot using malicious framework EHDevel and YTY.
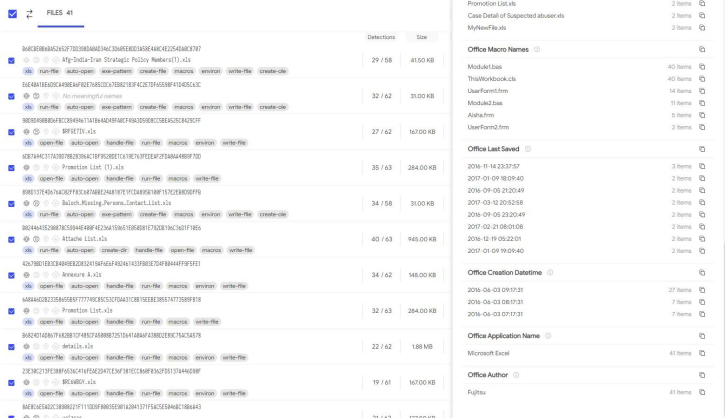
4.Comparing both samples, it is found that the sample size of TransparentTribe is significantly larger than that of Donot. The macro code of Donot is quite simple, while TransparentTribe has a variety of patterns. And in the captured historical activities of the two Groups, it is also found there are obvious traces of using the same template. The metadata and macro code are compared as follows:
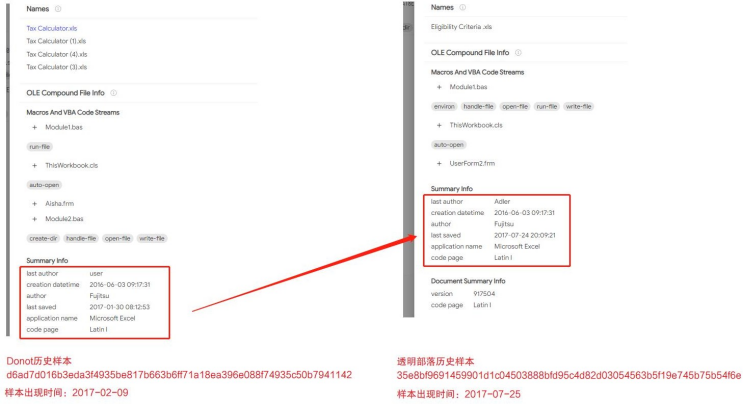

5.During the analysis of historical samples, it is found that the compressed packet files of some samples were uploaded from India. In the compressed packet, related samples of the TransparentTribe were also found.
Conclusion
The Group behind the attack discovered this time has been active for at least 13 years. The Group has capability of dual-platform attack and Trojan development. In the early activities, the Group uses Trojan. In the later activities, the Group mainly uses open-source Trojan. And assets are mostly dynamic domain names. In addition, during the sample correlation analysis, it is found that the Group has a certain overlap to TransparentTribe on attack targets and methods. The target mainly covered the Indian region in the early stages. With the signing of the Chabahar Port Agreement, all the countries involved were included in the attack range. Except for the three signatories of the Agreement, Iran, Afghanistan, and India, Baluchistan (the Pakistan-Iran border) near the Chabahar did not escape the attack range. What behind this attack is the interest conflict and competition among countries. The countries involved are basically located in South Asia and the Middle East, which are the area with high incidence of APT attacks. ThreatBook has always paid close attention to APT group from relevant areas, and will continue to track relevant APT attacks.

